Cybercrime Is Increasing at an Alarming Rate
Cybercrime is big business. The cost to the world’s economy from cybercrime increased 400% from 2013 to 2015, to over $450 billion. That is predicted to quadruple again to nearly $2 trillion by 2019. Even non-coders get involved in cybercrime because there are sites where turnkey hacking programs may be downloaded to attack others.
Cybercrime is a serious, and rapidly growing, threat. It’s not just large banks, financial institutions, and big retailers that are attacked, either. Microsoft reports that 20% of all small-to-mid-sized businesses have been targeted.
Many are fooled into complacency because they use antivirus programs. Studies show that antivirus products overlook 70% of all malware infections for the first 24 hours – and there are nearly one million new malware threats released daily. That’s a lot of malicious software gaining access to computers every single day.
Many users also feel that having user ID authentication requiring strong passwords is sufficient. There are a number of products that do this type of security very well. However, user ID authentication does nothing to protect user data, and it is not designed to prevent user account takeover.
Failing to protect against malware is like rolling the dice with your data. Sooner or later you are going to throw snake eyes. Cybercrime is so rampant that most experts feel it is not a matter of if you will be infected, it is a matter of when. However, there is something you can do to load the dice in your favor and better protect yourself from hackers.
The Solution: BlueGem end to end SSL
Studies show that since SSL encryption (https) helps protect data during transmission, 80% of all identity theft occurs at the vulnerable endpoints – that is, at your computer. The following image shows SSL encryption in your browser. You see this lock icon when you connect to secure sites.
Other tools available today provide some protection, but they fall short in different ways, creating critical security gaps. Antivirus programs miss detecting malware, network SSL ignores endpoints, and existing methods of user authentication are either costly or don’t prevent account hijacking. BlueGem Security’s solution closes those unprotected gaps.
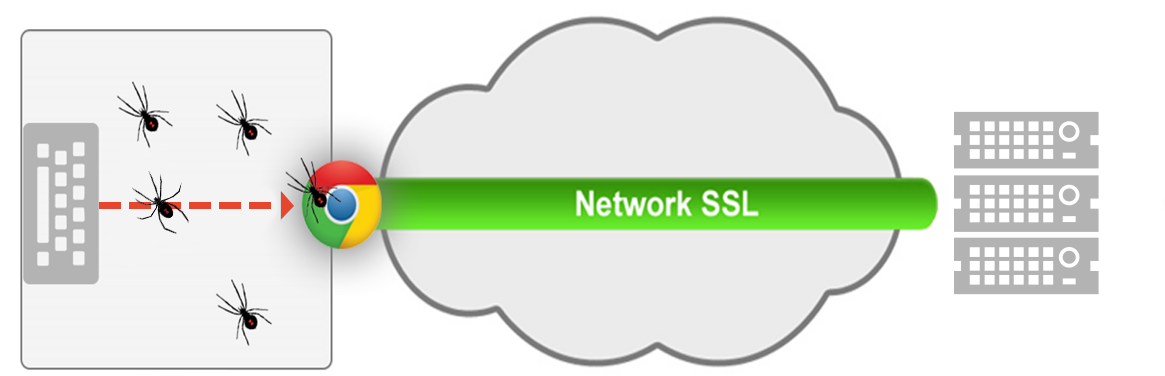
The following diagram shows the vulnerabilities in existing SSL technology. As you see, SSL only protects the user during data transmission with no extra protection at the server endpoint. However, the data has already been compromised at the user’s endpoint.
BlueGem Security’s end to end SSL extends SSL protection into the innermost level of your computer – right down to system chips. Every keystroke is securely encrypted with 128-bit encryption, which is virtually unbreakable due to the brute force required to crack it. This encrypted data is communicated to a cloud server through a secure channel. This end to end protection, from system chip to cloud server, ensures malware never has a chance to access or alter your data.
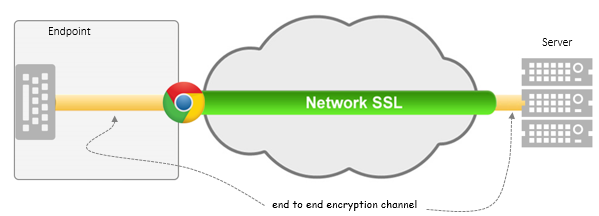
The following diagram shows how BlueGem end to end SSL is different. As you see, we extend another encryption pipe down to the source of user input (systems chip) and extend it to the cloud server, leaving no gaps where malware could intercept and steal user data.
User Data Verification Defeats Malware
There are existing solutions for securing user ID and password. However, you need to go beyond that because sophisticated malware exists that defeats this type of security. This attack is different from trying to hack user authentication - in fact, this insidious malware just goes around the security user authentication provides. The hacker uses malware to intercept phone numbers, Social Security numbers, email addresses, and other profile data, and alters them to ones the hacker can use. For example, intercepting and altering the cell phone number being entered in a user profile page lets the hacker receive messages that would allow the user password to be changed, without the need to crack the original password. Hackers can also sell the information gathered, sometimes making millions of dollars from stolen data.
BlueGem Security’s solution is designed to specifically prevent bypassing user authentication to takeover user profiles. When user profile data is entered, the authenticity of the data is always verified by the BlueGem application, and the user is alerted when there is an attempt to manipulate the data. Other methods try to provide protection at the User ID/Password level, but malware can bypass that. With BlueGem Security’s unique end to end SSL with user data verification, users can feel confident that the integrity of any entered profile data is protected.
Solution Is Easy to Use
Existing solutions that attempt to contain malware are too costly, intrusive, or affect the performance of the computer. Some are so difficult to understand and implement that they require extensive - and often expensive - training. BlueGem Security’s secure end to end SSL is unique because it eliminates these problems.
There is no training necessary to use BlueGem Security’s end to end SSL software, nor does the user have to change any procedures or habits. Continue business as usual, and end to end SSL quietly works in the background.
BlueGem Security’s end to end SSL helps companies and individuals meet compliance with the ever-growing regulations and rules overseeing many industries. It provides an additional layer of protection, yet, it doesn’t require any restructuring of existing infrastructures.
Contact BlueGem Security for Peace of Mind
End to end SSL provides multiple layers of protection, closing the gaps other security measures fail to address. And it does it efficiently and securely without compromising computer performance or requiring a complicated user learning curve. For more information about how end to end SSL can lock down your data from creation to delivery and keep out malware, contact BlueGem Security at www.bluegemsecurity.com today!
HOME